Credential Technology for Improved Access Control

Cards and readers have come a long way since they were first introduced to the market. Despite the growing availability of newer and more secure options, many organizations are still using outdated and vulnerable access control technology.
For most organizations, now is a good time to consider upgrading to the next generation of credential and access control technology. There are three key factors behind this:
- Growth and maturity of newer credential technologies
- Secure bidirectional access reader and panel communication
- Improved economics of new credential and reader technology
Life Cycle View
Life cycles for credential and access control technology are long by comparison to many industries. As such, it is important to understand these life cycles in the context of investment decisions being made. Our examination of these life cycles yields the following conclusions:
- Credential technology typically has a 20 plus year lifecycle.
- Within that lifecycle, major development periods happen every 5-10 years. These development periods have been especially driven by the need for improvements and safeguards against security vulnerabilities.
- Once a new credential technology (major development) is announced, there is generally a three to five-year ramp-up period before that credential technology becomes prevalent in the market. Interestingly, all major manufacturers are roughly on the same life cycle timing which reflects the emergence of underlying technologies that drive these life cycles.
- Access control systems tend to have 10-15 year lifecycle once deployed (thus the need for elongated credential technology life cycles that span a range of installations).
Recognizing and considering these lifecycles can help guide the timing of investment decisions. The chart below provides an overall view of credential technology lifecycles. Looking at this along with an in-depth view of credential product family developments shows maturity levels and how a major shift toward second generation smart cards and mobile credentials is now upon us.
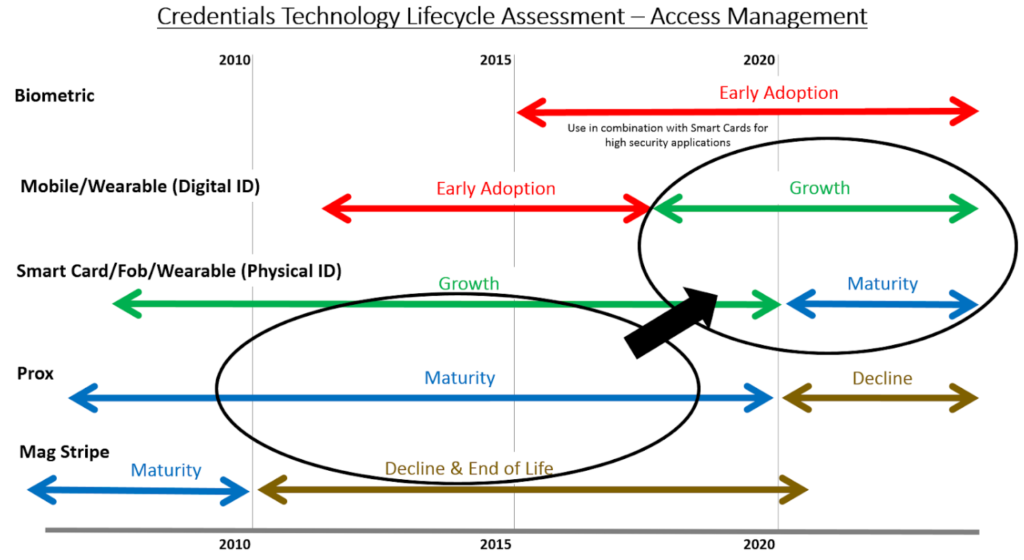
Credential Technology Landscape
The primary issue with the majority of credentials used today is their vulnerability to being copied and/or hacked.
Magnetic Stripe (Magstripe)
These cards contain a strip of magnetic recording tape on the outside of the card that is swiped through a reader. Magstripe cards have been standard in the industry for years and are still commonly used in legacy installations for access control together with other identity related applications. Cost has prevented a shift to newer technologies in the past, although the cost advantages are no longer viable relative to the significant security vulnerability and lack of availability of these systems. In summary, although inexpensive, magstripe credentials have very low security and have a limited amount of information stored on the card.
Proximity Cards (Prox)
Prox cards are the standard in most access control systems today. They use a radio frequency (RFID) to communicate between cards and reader and have been in use since the 1980s. Prox cards are easily copied via inexpensive scanners that can extract the information on a prox card and duplicate it on one or more blank cards. While easily available, prox cards offer very little security to your building because of how easily the credentials can be cloned.
Smart Cards (First Generation)
Smart cards work at higher radio frequencies then Prox cards and have considerably more memory capacity (up to 800 times that of a magstripe and 100 times that of prox) which allow them to securely encrypt data and function in other applications. Both the credential and the reader contain a set of cryptographic keys that allow for mutual authentication through a complex mathematical process to compare keys.
Credential Technology Landscape – New Generation
The industry has evolved to offering newer and more secure credentials to the marketplace such as iCLASS SEOS (HID Global) and MIFARE DESFire EV2 (NXP and other suppliers). These newer technologies have gone through the initial adoption and refinement period which has propelled these technologies towards growth and maturity life cycle phases, which has also aided in decreasing costs.
Smart Card (Generation 2)
Many first-generation smart cards became vulnerable over time, which led to a new wave of smart card technology starting around 2015. This new wave of smart card credentials differs from the previous in two areas: security and applications. Todays’ credentials feature open and widely adopted security standards for encryption that were not available in the first generation. The newest smart cards continue to enable a large number of applications in addition to access control, however, are designed to do this in a way that does not expose the core identity information and encryption to these other applications (for example food purchase and other auxiliary services).
Mobile Devices
Steps have been taken to allow for fully secure credentials on mobile devices. The benefits are clear – there is a convenience for users (employees, students, etc.) for having fewer items to carry and remember, and since few people go anywhere without their phones, lost or forgotten credentials are greatly reduced. Mobile credentials also make the administration of access control easier through streamlined digital processes. They can be upgraded without issuing a new physical identification and linked to other phone services and applications like geofencing.
Most mobile credentials are either Bluetooth Low Energy (BLE) or Near Field Communication (NFC) based which has become the prevailing mode for mobile related access communications.
There are some practical factors to consider when using mobile credentials. These include supporting use in BYOD environments, device and credential ownership, users changing devices, and low/dead batteries.
Biometric Credentials
While biometrics like fingerprint reading, iris and facial recognition have been around for some time, application of these for access control is still in an adoption phase as the technology evolves and the accuracy and practical use factors continue to improve. There are many companies working on facial recognition for access control. By comparison, there are three to five major providers of smart card technology for access control. This is a typical difference comparing emerging technologies/products with maturing. Cost and throughput are still significant barriers to adoption.
Most adoptions of biometrics are done in combination with smart cards. Biometric data is stored on the individual smart card which allows it to be compared with the biometric read to provide an extra layer of identity management and security. Furthermore, this reduces the risk of having the personal biometric data exposed in devices or software systems.
Hybrid Approach
The choice of credential technology doesn’t have to be a single selection. Many are considering a combination of smart card and mobile credential technology and possibly adding in biometrics in situations requiring the utmost of security. Multi-technology readers, including electronic locks, continue to be readily available which makes a hybrid approach feasible.
Access Control Reader – Panel Communication Developments
There is more to consider than just the credentials themselves – changes in credentials impact readers, electronic locks, wireless locks, and possibly even control panels and the future interoperability of the security and access control system. One of the important developments that enhance the value of using next generation smart cards and mobile credentials is the two-way (bi-directional) communication between the readers and access control panels following the OSDP (Open Supervised Device Protocol) standards set by the Security Industry Association. The biggest advantage of this is the AES-128 encryption between reader and panel that removes vulnerabilities at the reader station. Additionally, bi-directional communication can be used to send firmware updates to readers without having to perform this function at each reader. For example, should a future vulnerability be found in a mobile credential, it is not only easy to distribute updates to the mobile credential itself, but also to flash update all readers from the panel(s) to accept the updated credential and thus significantly reduce the response time to a discovered vulnerability.
Is the Timing Right for Our Organization to Update?
While every situation is different, for most organizations it is a good time to consider updating to the newer credential and access control technology. Smart card technology is in a mature phase and mobile technologies are increasing growing and developing into stable solutions. The initial phase of recent generation product release and ramp-up is mostly complete and there is not likely to be a major change for the next five years. History has shown that the life cycle of these technologies will extend for a significant time period in the future (15+ years) which reduces the risk of any short-term decision. Most new readers and panels are compliant with OSDP. Furthermore, many organization are investing heavily in cyber security and without upgrading to new technologies, access control credentials will become the weakest link in protecting these cyber assets. Moving forward allows organizations to significantly improve their security and take advantage of the newer technologies for convenience.
Another factor in favor of moving forward is the availability of open solutions to help ensure future upgradeability as well as supplier choices to keep costs from escalating.
Contact us to learn more about the latest credential and access control technology.
Authored by Mike Traniello, Vice-President Customer & Solution Management, and
Tony Barbeau, Director of Marketing & Business Development, at TSG Security



















