Access Control Solutions
Top notch security should be suited to you – that’s why we take such a custom approach when it comes to access control. Whatever you need secured, whether it be doors, windows, gates, or assets, we can design a system that meets your needs.
- Scalable from a single door to a global enterprise size system
- Open architecture system, so you’re never locked into proprietary hardware
- Comprehensive integration with other security and safety systems, such as video surveillance and intrusion alarm monitoring
- Support any credential technology
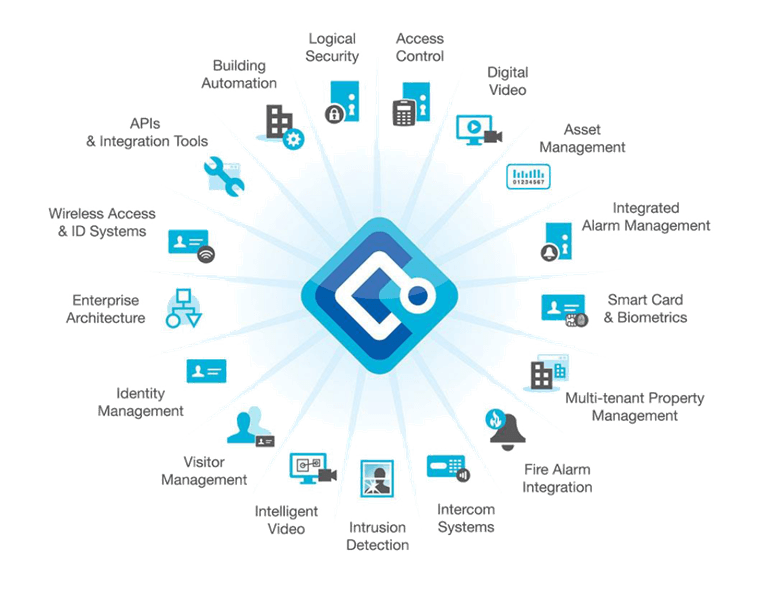
Our Focus is on a Complete Solution
TSG Security was created as an alternative to faceless, large, national suppliers. Our goal is to give customers the benefit of choosing different solutions from various vendors to meet exacting needs. This was a revolutionary idea in a market saturated with proprietary systems and poor service.
Our focus is on finding a complete solution and building a system that works together seamlessly, integrating whatever type of security you and your organization need most.
Custom Solutions
Cost Effective
Long-Term Results
Access Control Card Reader and...
Transition Access Control Proximity / Legacy Technology to High Frequency Credentials The vulnerability of Proximity type card access credentials has been known for several years now. Proximity credentials are easily...
How to Test and Maintain...
Fire safety is essential – nobody doubts this. Some people believe that a well-designed system straight from the manufacturer is sufficient, but unfortunately, it is not. Commercial fire alarm systems...





















