Upgrading Access Control Credentials
For many organizations, over time, access control requirements required updating to a variety of electronic technologies because:
- The organization has scaled, making it impractical to manage large numbers of physical keys.
- The value of assets being protected has increased and requires a higher level of security than keys alone can provide.
Although electronic access control systems can provide enhanced security and lower costs, recent exploits of vulnerable security credentials demonstrate the need to update a large number of access control technologies currently in use. These include many types of security credentials, ranging from Magnetic Stripe, Proximity (Prox), and Smart Cards/Fobs. Many organizations, including yours, may still be at risk for unauthorized access and hacking by bad actors.
But how do you migrate to a more secure system without running into major inconvenience or cost issues? After all, upgrading your access control system requires making informed decisions that are critical to:
- Create the level of security that delivers the right “fit” for your organization.
- Promote interoperability within the access control platform and with your associated systems, such as time keeping, vending, food service, logical access control systems and more.
- Optimize solutions based on your available budget.
- Recognize proprietary solutions and evaluate their impacts on your organization.
- Develop and execute a long-term strategy to minimize costs for future upgrades.
TSG Security's experts will help you make smarter choices.
Why isn’t my current card reader system secure?
Many widely deployed access control credentials (cards, key fobs and others) are easy to duplicate. In fact, in some cases it can be easier to discreetly copy an access control credential than it is to copy a physical key. The vulnerability of these credentials then makes these access control systems ineffective.
Even if you’ve upgraded your access control, your organization’s users may not be aware that your current technology can still be vulnerable to duplication. TSG has learned that many customers have moved off vulnerable credential technologies to supposedly secure technologies, only to find that the newer credentials don’t provide the additional security they intended and assumed. Unless the system is properly configured and deployed, even new credentials may be vulnerable to duplication and used to gain unauthorized access.
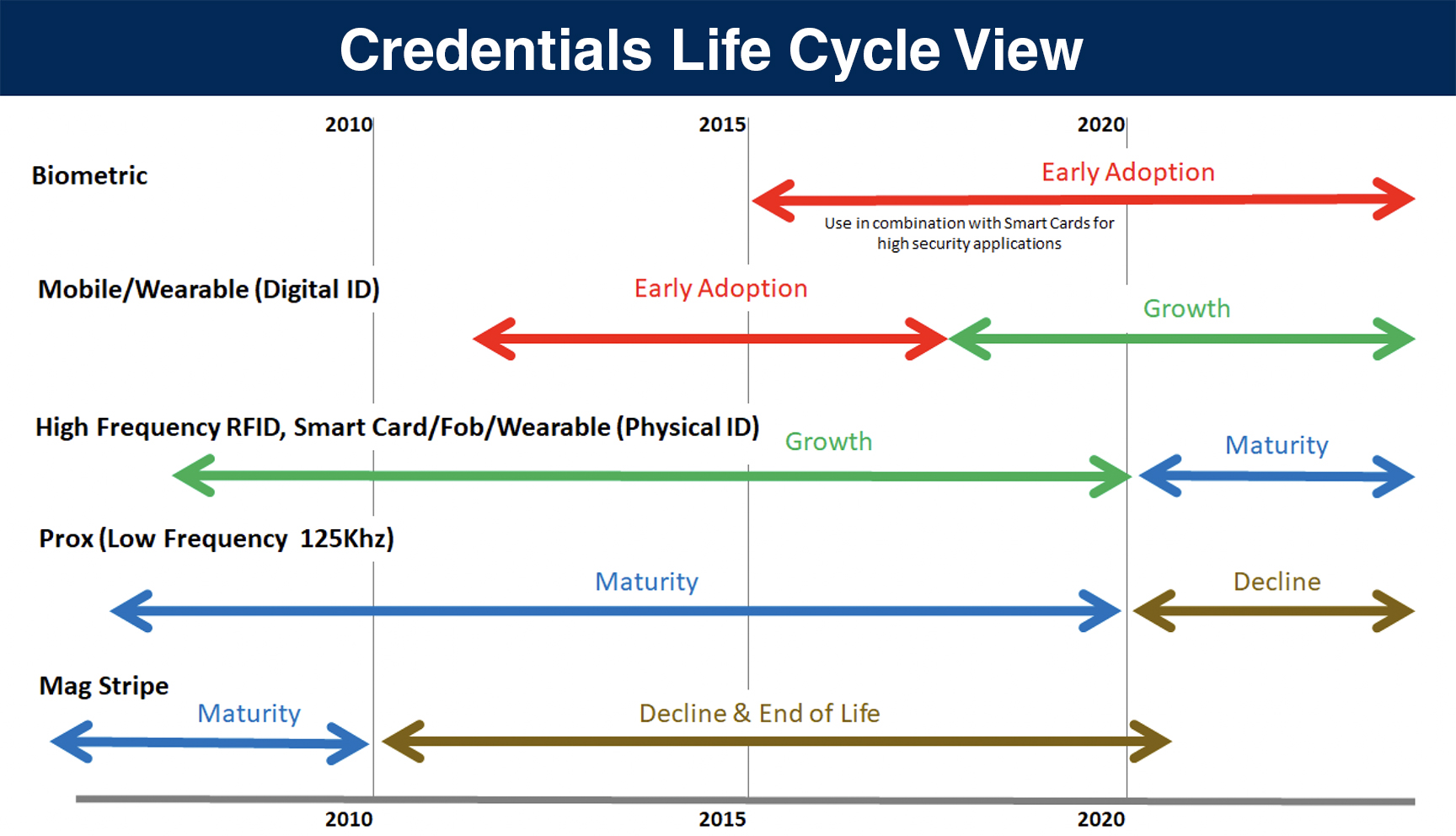
What makes high-frequency Smart Cards more secure?
Security professionals have known about the vulnerability of low-frequency card access credentials such as Prox cards for several years now. Proximity credentials are easy to duplicate with inexpensive, readily available cloning devices.
At TSG, we’ve advised our clients to replace Proximity credentials with more secure, high-frequency credential technologies. While there are many options for credentials that offer higher security, many clients choose to use a high-frequency credential commonly referred to as Smart Card technology. Smart Cards are a preferred choice since the user experience is the same—the card or fob is simply presented within a few inches of the card reader. Reading the card in either case involves no contact offers identical functionality to the user.
The advantage of high-frequency credentials is that the card data can be secured through encryption and other methods. But even though encryption makes it more difficult to duplicate the credential, it’s still possible to clone high-frequency credentials. So it’s important to understand the additional steps necessary to ensure their security, even with a move to high-frequency credentials.
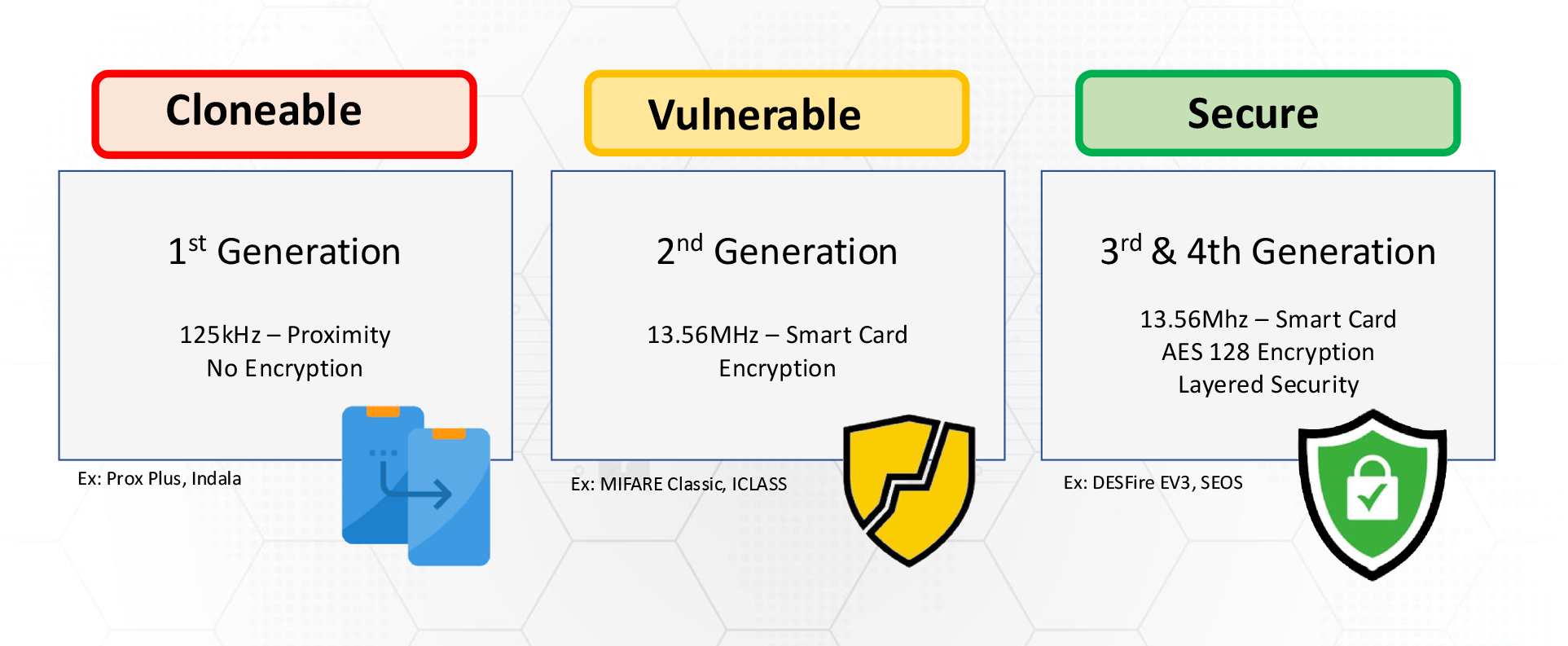
What additional steps are required for increased credential security?
Physical security applications predominantly use what is called a key exchange for authentication. The credential and the reader need to perform what is called a “handshake” to exchange keys. Most often, symmetric key exchange is used by physical access control systems. This means that the reader and the credential share the same key and they authenticate each other by exchanging their keys.
For increased security, it’s important to understand the types of keys available and how they’re implemented in physical security applications. Manufacturers’ standard keys, even with the use of high-frequency credentials, may still be vulnerable to duplication. It’s important to consider the various options for key authentication to make informed decisions. It’s possible, although not always practical, for users to create and maintain their own private key for enhanced security. There are also several manufacturers that offer custom keys, which have been proven to offer enhanced security.
So would it be better to use our mobile phones instead of cards or badges?
Mobile credentials provide advantages in convenience and security. They may be a good choice for some organizations’ users, but not all. The primary advantages of mobile credentials are that they’re easy to upgrade remotely to each user’s device, and they inherently include multifactor authentication (MFA) for enhanced security.
However, they aren’t a good fit in security applications where a photo ID is also required. At TSG, we also advise clients about the need to support users’ personal mobile devices in Bring Your Own Device (BYOD) environments to prevent security breaches. Some of our clients have found that a hybrid environment, with a mix of mobile and physical credentials, is best for their organization.
When you’re planning for a credential replacement, it’s important to consider mobile credentials and integrate them for future use. Recent reports show that mobile credentials may be the answer to having physical access control solutions use asymmetric encryption in addition to a Public Key Infrastructure, which is more secure than the symmetric key exchange used in today’s physical access control solutions.
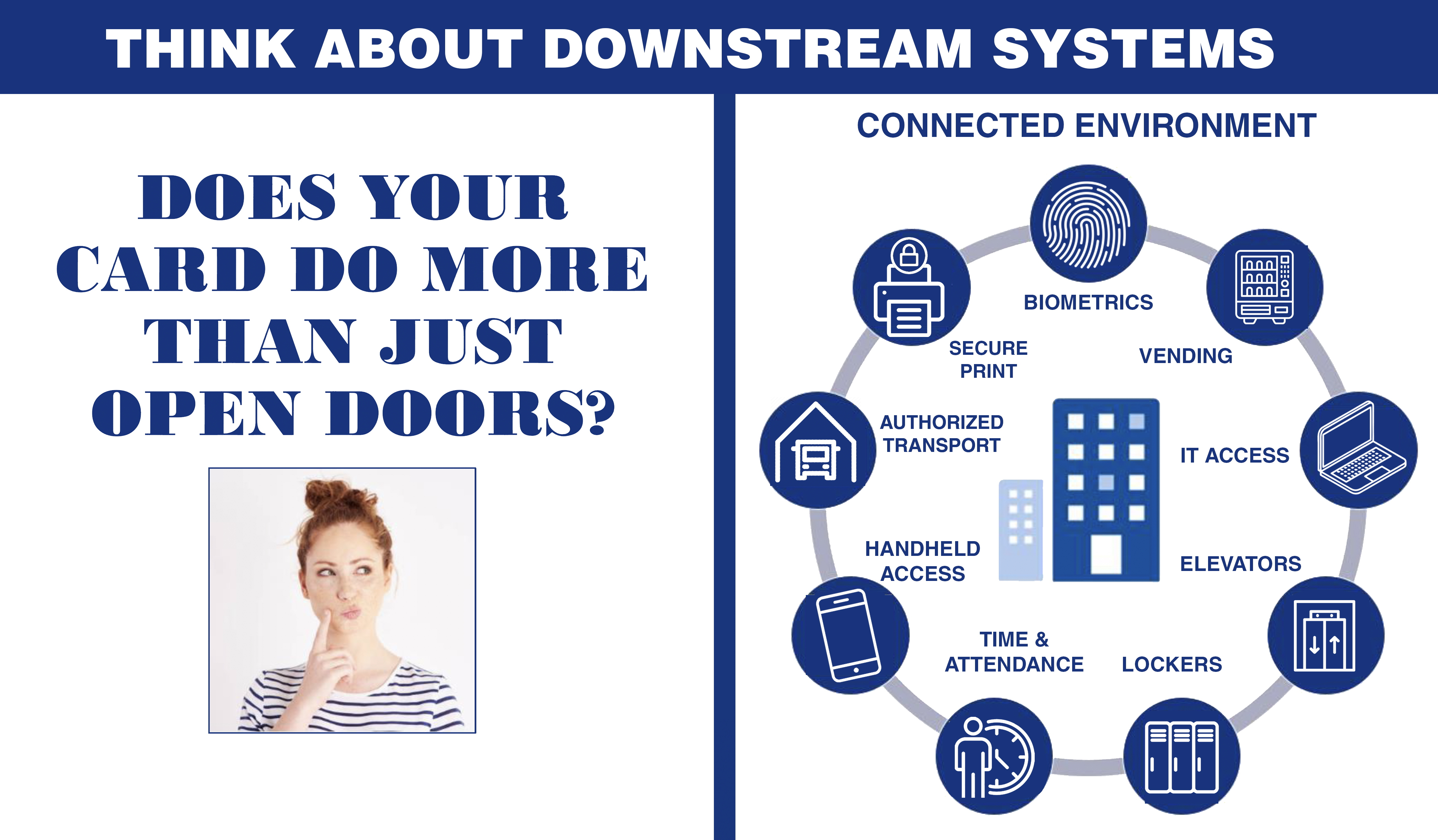
How do the different credential technologies affect a system’s operations?
There’s a wide variety of credential formats and digital keyset options on the market for physical access control. For most clients, the best options provide both protection and interoperability. But the information available to system owners to perform this evaluation can be misleading. We advise system owners to understand both their current environment and the interoperability requirements for any option worth considering.
Here’s why: A credential may appear to be “open” and provide the interoperability you want, but may also require users to share or expose the keyset to create that interoperability. This may not be a concern for your organization, but if you need a higher level of security in specific environments, it may be best to avoid sharing that keyset information, even with the manufacturer.
At TSG, we have extensive experience with many user segments that require various levels of security and can advise you on best practices, based on your goals.
Are credential security and interoperability the only concerns when we upgrade our physical access control systems?
By choosing an encrypted credential technology, you can protect access card data at rest and in transit to the card reader, which is the first step in developing better security for your operations.
But it’s also important to note that card data can still be susceptible to an attack from the card reader to the access control panel. Similar to card skimmers that are installed on ATMs and gas station pumps, card skimmers can also be installed to capture card data at the reader.
Best practices for reader installation would include wiring and monitoring the reader tamper, but for enhanced security and future flexibility, wiring your card readers for Open Supervised Device Protocol (OSDP) provides encryption from the card reader to the access control panel. It also provides bi-directional communication to the readers. And if a keyset needs to be changed, a new key can be rolled out to the reader, which eliminates the cost of replacing the reader.
So what do we need to consider before any security technology upgrades?
Before you invest in a new or upgraded enterprise security system, it’s critical to review:
- Your specific security needs for property, employees, contractors and visitors.
- The level(s) of access control you need, per your industry and personnel’s responsibilities.
- All federal and local regulations for your industry, to ensure compliance and insurance coverage.
- Compatibility with your existing systems.
- Any necessary monitoring options.
- Installation costs along with ongoing maintenance needs and costs.
- Your growth plans for the future, including any additional locations.
These are all essential considerations to ensure alignment with your business or organization’s requirements along with your budget. It’s very important to consider system scalability to accommodate future growth—you don’t want to be locked into a technology platform or products that will require completely new replacements and the associated additional expenses. Every security solution requires the right balance of security, convenience and cost for a specific organization.
That’s why TSG is the smart choice for your enterprise security management system. We specialize in integrating customized choices for access control, intrusion alarms, fire detection, visitor management, electronic locking, communications and other security technologies into a connected, universal platform with a common user interface. The platform allows all the subsystems to communicate with one another so that it acts as one operating unit, providing you with a greater level of protection, convenience and ease of use.
TSG’s experts have the extensive experience to help you make informed decisions about access control credentials. We offer solutions from all of the industry’s leading suppliers—which also means that we can provide you with impartial analysis and guidance.
At TSG, we recognize the need to always look beyond the credentials themselves to the big picture—your entire system. Our highly knowledgeable and experienced staff can show you how every function of your system can work together by integrating the right components to deliver the most reliable, flexible, and cost-effective long-term solution, saving you time, money and inconvenience. Call or contact us today for a meeting at no obligation.



















